November 15, 2021
Armasuisse Car Hackathon and Research Visit
Richard Baker and Sebastian Köhler spent a week attending a car hackathon arranged by Armasuisse Science+Technology, in Thun, Switzerland. There were instructional sessions with experts from WhiteMotion, along with hands-on vehicle-hacking days to try out attacks on a range of vehicles. The Oxford team developed an attack to disable the driver instruments in a Nissan Leaf while driving, along with programmatic control over drive mode, vehicle stability programme and headlamp activation. They then fooled the traffic sign recognition system on a Renault Zoe, to accept homemade signs that were printed or projected for the camera.
Over the course of a second week, the trip was also an opportunity to test attacks on vehicles that are being developed in the Systems Security Laboratory here at Oxford. The team was first able to reproduce the rolling shutter effects of their new ACSAC paper [1] on a Renault Zoe. They also then tested new attacks against the EV charging process, investigating the requirements for attacks to be conducted remotely.

Spoofed speed limits in a stationary Renault Zoe

Spoofing temperature reports in a Nissan Leaf
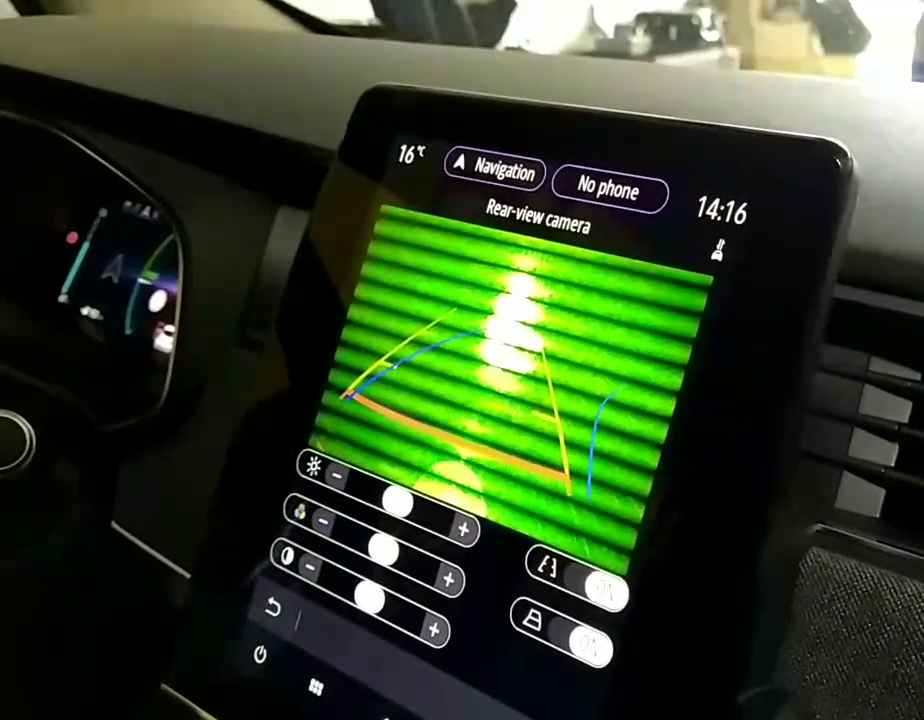
Rolling shutter attack on a Renault Zoe

Fast-charging a Renault Zoe
[1] Köhler, Sebastian, et al. “They See Me Rollin’: Inherent Vulnerability of the Rolling Shutter in CMOS Image Sensors.” Annual Computer Security Applications Conference, 2021.
